Cloud Services¶
Franz Marc, "Spielende Formen", 1914Current usage of electronic data safes ( PhD project)¶
Applied methods & measures
UX research methods: qualitative research, interview study with a semi-structured interview guide, transcription, thematic analysis, MAXQDA
Measures: net promoter score
Kernel theories: Transactional Model of Stress and Coping (TMSC)
Goal: Analyze how an electronic data safe (EDS) (related to the project Data Purse) fits into an individual’s information ecology. Furthermore, the participants in an interview study were asked about their current practices for shaping a digital legacy.
Approach: This project was based on qualitative interviews with 39 participants using thematic analysis as a research methodology and MAXQDA as tool support. A semi-structured interview guide (pre-tested) has been used to collect data. In total, 39 interviews have been conducted (31 in German, 8 in English) resulting in 53 hours and 02 minutes of audio data. On average, an interview’s duration is 1 hour 19 minutes and it contains a net number of 4079 words without the questions asked. For analyzing the digital legacy part, the Transactional Model of Stress and Coping (TMSC) as an analytical lens was used. Furthermore, the net promoter score was applied to the interview participants during the interviews.
Findings/Results: A typology of the content that is kept safe in an EDS is developed; it is reflected upon the motivations and upon an EDS’s role with respect to other cloud-based storage services individuals are using; challenges of maintaining a digital, personal archive are depicted and “data value zones” are introduced as a sensitizing concept to reflect upon problematic areas.
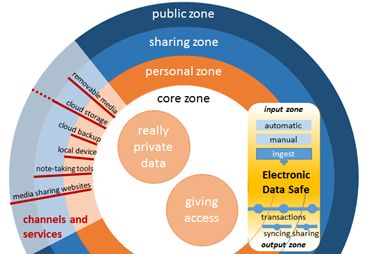
Data Value Zones
Pre-mortem password sharing is identified as a common problem-focused coping strategy. Moreover, emotion-focused strategies of avoidance and ignorance are discussed. I suggested that the well-established TMSC-model explains behaviour described in the literature as benign neglect. Further challenges of shaping a digital legacy are described and discussed to, finally, develop design implications. Please see the publication section for details on the findings and results.
Role of Joachim Pfister: Developing the research plan, project management, participant recruitment and administration (involving cross-organizational coordination), development and pretesting of the interview guide, data collection, transcription of the interviews, data analysis, writing reports for project stakeholders, writing the publications, preparing conference presentations, presenting at one conference.
UX research challenges successfully addressed
- Creating a trustworthy interviewing environment that allowed the interview participants to open up and share
- their personal information management practices with successes and failures, as well as
- the contents of their electronic data safe (data of utmost personal importance because it is put into an electronic safe).
- Discovering approaches for sharing a digital legacy which arose as unexpected findings in the data.
- Applying an established theory from psychology to understand and explain observations and to derive future design recommendations.
- Identifying different zones of value for personal information in an electronic data safe and other cloud storage services.
- Interview guides for the semi-structured interviews ( Service 1, Service 2)
- MAXQDA screenshot for doing thematic analysis / grounded theory
 Due to confidentiality reasons, no actual data is presented. Instead, a screenshot from MAXQDA's manufacturer is presented. Source: https://www.maxqda.com/wp/wp-content/uploads/sites/2/MAXQDA-12-Englisch.png
Due to confidentiality reasons, no actual data is presented. Instead, a screenshot from MAXQDA's manufacturer is presented. Source: https://www.maxqda.com/wp/wp-content/uploads/sites/2/MAXQDA-12-Englisch.png
-
Pfister, Joachim; Schwabe, Gerhard (2016): „Going Paperless with Electronic Data Safes: Information Ecology Fit and Challenges“. In: Proceedings of the Thirty Seventh International Conference on Information Systems. December 11 – December 14 2016. Dublin, Ireland. (PDF online @ institutional repository of University of Zurich)
Abstract of: Going Paperless with Electronic Data Safes: Information Ecology Fit and Challenges
In private households, once received paper-based documents are increasingly substituted by electronic documents. In order to “get organized”, an individual nowadays needs to oversee a plethora of digital and physical information items stored at various locations. As a technological solution, cloud-based storage services such as an Electronic Data Safe (EDS) emerge as a home for all digital valuables. In this paper, we analyze how such an EDS fits into an individual’s information ecology by drawing upon the results of a qualitative interview study with 39 users of three different EDS services. We develop a typology of the content that is kept safe in an EDS, reflect upon the motivations and upon an EDS’s role with respect to other cloud-based storage services individuals are using. The challenges of maintaining a digital, personal archive are depicted and “data value zones” are introduced as a sensitizing concept to reflect upon problematic areas.
-
Pfister, Joachim (2017): “’This will cause a lot of work.’ – Coping with Transferring Files and Passwords as Part of a Personal Digital Legacy”. In: Proceedings of 20th ACM Conference on Computer-Supported Cooperative Work and Social Computing. February 25- March 1 2017. Portland, Oregon, United States. DOI: 10.1145/2998181.2998262.
Abstract of: „This will cause a lot of work“. – Coping with Transferring Files and Passwords as Part of a Personal Digital Legacy
We present a qualitative interview study of 39 participants who describe their current practices and concerns with shaping a digital legacy, especially when they are using cloud-based storage services that unify secure file storage and password management functionalities in one service (electronic data safes). After introducing the transactional model of stress and coping as an analytical lens, we report on the users’ coping strategies with respect to shaping and giving access to their digital legacy. Pre-mortem password sharing is identified as a common problem-focused coping strategy. Moreover, emotion-focused strategies of avoidance and ignorance are discussed. Challenges associated with passing on a digital legacy, such as the lack of enculturated practices, difficulties in the appraisal and selection of information items, the preference for deletion, and implicitly transferring data stewardship duties are described and discussed to develop design implications.
Developing and evaluating a prototype for an electronic data safe ( PhD project)¶
Applied methods & measures
UX research methods: explorative research with an interview study and a software prototype, setting up and using quasi-realistic scenarios and tasks for test participants, qualitative research based on interviews with a semi-structured interview guide, thematic analysis, MAXQDA, AXURE
Data Analysis qualitative and quantitative analysis for the measures listed below.
Measures: user acceptance, willingness to pay
Communicating findings using: written reports, AXURE mock-ups, conference publications, presentations
Goal: Identify challenges for solutions supporting a transformational government that follows the paradigm of user-managed access based on a user study with ordinary citizens.
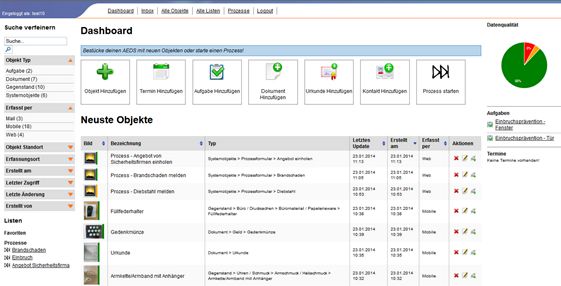
Step 1 - Preliminary need-finding studies: An interview study (unpublished) with 17 participants was carried out by Joachim Pfister to research their personal information management practices with regards to receiving and caring for digital or conventional, paper-based mail and an individual's administrative burdens with authorities (for instance, taxes). The interviews were not fully transcribed but essential observations were summarized and synthesized. These observations were used to identify pain points/requirements with respect to organizing oneself and one's paperwork. They served as inputs for the requirements/goals of a prototype of an electronic data safe. A storyboard was designed by a fellow PhD-student. A clickable prototype with Axure was developed by Joachim Pfister to be used for discussions with the project partners.
Step 2 - Ideation: Two Master's students who were supervised by Joachim Pfister designed and programmed a prototype of an electronic data safe consisting of a mobile app (Android) and a web-based application. During the ideation phase, competitive analysis for identifying best practices of existing solutions for personal information management were used. Furthermore, formative evaluations using paper-based prototypes were carried out which were accompanied by Joachim Pfister. Elements of design thinking were used to ideate solutions for the identified problems.
Step 3 - Evaluation Approach:

Twelve citizens and three representatives of public and private sector organizations (the police, an insurance company, and a security company) were involved in an exploratory user study to research their interactions with a prototype of an electronic data safe in a lab-based setting. The participants carried out three (end-to-end) business processes and underwent a semi-structured interview afterwards. The interviews were transcribed and analyzed using a thematic analysis approach. Furthermore, user acceptance and the willingness-to-pay was measured, too. SPSS and Excel were used to master the statistics and to look for correlations.
Findings/results: Four barriers for the adoption of an EDS in the light of transformational government were discovered (please see the publication section for details on the findings and results):
- offering citizens unfamiliar services having the character of experience-goods;
- failing to fulfil common service expectations of the customers;
- failing to establish contextual integrity for data sharing; and,
- failing to establish and run an active EDS as a multi-sided platform providing an attractive business model.
Role of Joachim Pfister: Developing the research plan, project management, participant recruitment and administration, adapting the existing prototype originally developed by the Master's students (Web application and Android app), developing the interview guide, the evaluation measures and the participant's manual for the tasks that they needed to perform, data collection, transcription of the interviews, data analysis, writing reports for project stakeholders, writing the publication, preparing the conference presentation and presenting.
UX research challenges successfully addressed
- Immersing test participants quickly and deeply to gain rich feedback for the yet unknown service.
- Involvement of real-life stakeholders to evaluate user-generated information items by the test users.
- Providing estimates on the willingness-to-pay for a yet unknown service.
Evaluation approach visualized

Room for the evaluation


Storyboard on paper
Clickable mock-up in AXURE
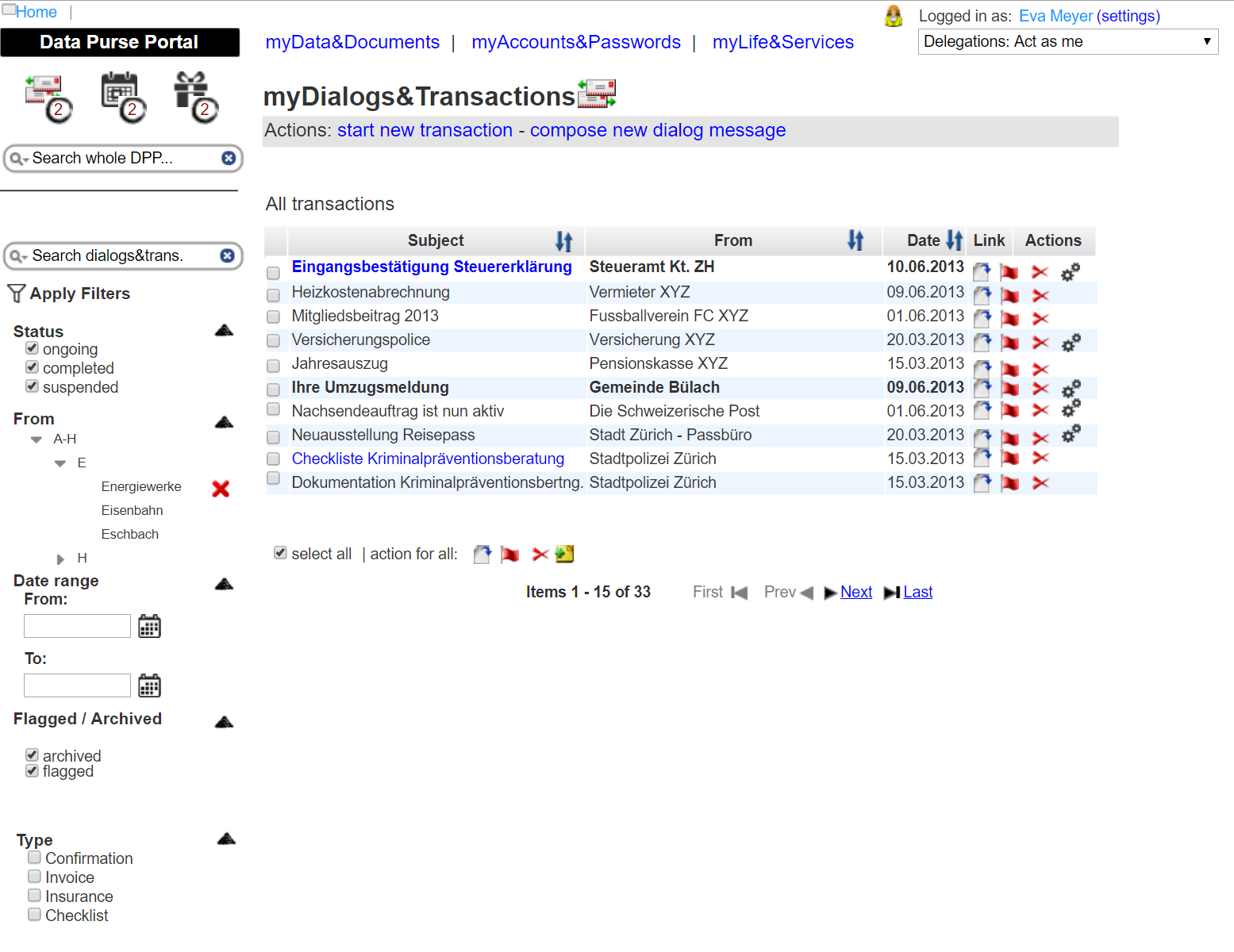
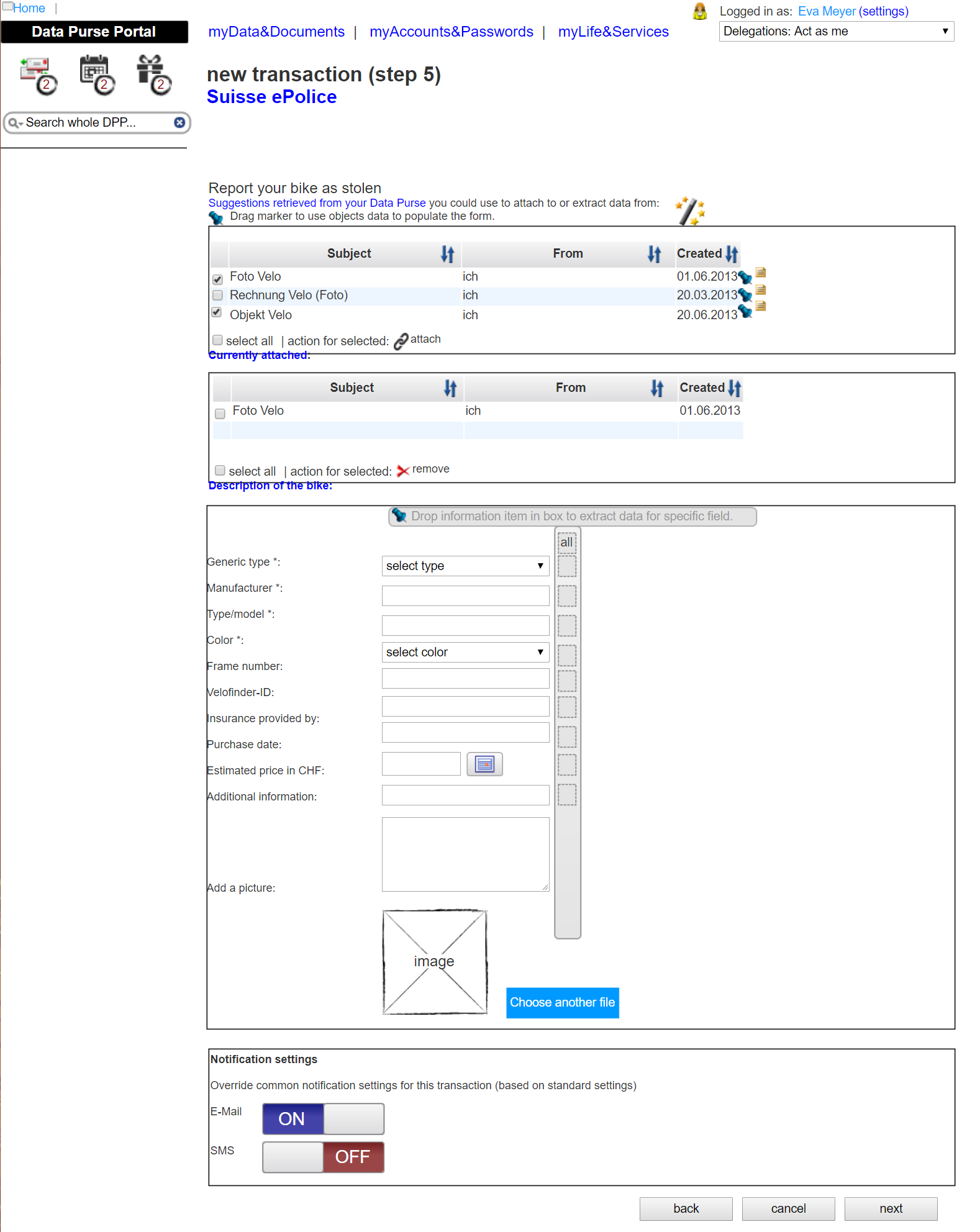
Web-based portal of the evaluation prototype

Mobile part of the evaluation prototype
Pfister, Joachim and Schwabe, Gerhard (2015): „Electronic Data Safes as an Infrastructure for Transformational Government? A Case Study“. In: Tambouris, Efthimios; Janssen, Marijn; Scholl, Hans Jochen; Wimmer, Maria; Tarabanis, Konstantinos; Gascó, Mila; Klievink, Bram; Lindgren, Ida; Parycek, Peter (Eds.) Electronic Government, 14th IFIP WG 8.5 International Conference, EGOV 2015. Thessaloniki, Greece. Proceedings. Springer International Publishing, Cham. pp. 246–257, DOI: 10.1007/978-3-319-22479-4_19. (PDF online @ institutional repository of University of Zurich)
Abstract of: Electronic Data Safes as an Infrastructure for Transformational Government? A Case Study
This article introduces and explores the potential of an active electronic data safe (AEDS) serving as an infrastructure to achieve transformational government. An AEDS connects individuals and organizations from the private and the public sector to exchange information items related to business processes following the user-managed access paradigm. To realize the transformational government’s vision of user-centricity, fundamental changes in the service provision and collaboration of public and private sector organizations are needed. Findings of a user study with a prototype of an AEDS are used to identify four barriers for the adoption of an AEDS in the light of transformational government: (1.) offering citizens unfamiliar services having the character of experience-goods; (2.) failing to fulfil common service expectations of the customers; (3.) failing to establish contextual integrity for data sharing, and, (4.) failing to establish and run an AEDS as a multi-sided platform providing an attractive business model.
State-of-the-art report on electronic data safe solutions ( PhD project)¶
Applied methods & measures
UX research methods: expert interviews (some conducted remotely) using a semi-structured interview guide, competitor analysis
Methods for analyzing data: document analysis, interview transcriptions, service business model canvas as an extension of the business model canvas
Communicating findings using: written reports, conference publication, presentations
Goal: This project aimed at refining the concept of electronic data safes for managing personal data and describes the landscape of existing services. Factors and areas of interest are identified that are relevant for the adoption of electronic data safes in e-government and e-business (related to the Data Purse project).
Approach: This project used an exploratory research approach. Data sources were a literature analysis, a document analysis, and qualitative interviews with experts based on a semi-structured interview guide. Sense-making was performed by compiling an intermediary report. Factors relevant to adoption were analyzed using the Unified Theory of Acceptance and Use of Technology as a theoretical lens.
In my PhD thesis, I updated and extended the original research for existing services by adding further services and updating their service business model canvas in order to derive new information by comparing the different services.
Findings: The model of hierarchical service layers was introduced which is assumed to be applicable in other contexts where data management and data processing are decoupled. Factors and areas of interest which might serve as facilitators or barriers for the adoption of electronic data safes were identified.

Hierarchical Service Layers
Role of Joachim Pfister: Developing the research plan and interview guide, project management (assisting the primary investigator in setting up a project plan, controlling the budget, identifying dependencies with other work packages, and coordinating fellow researchers and external stakeholders, assisting the PI in writing a successful research grant to fund this project, and communications with the funding agency, for example, related to the periodic and final reports, and the preparation of the grant), participant recruitment and administration, data collection, (partial) transcription of the interviews, data analysis, writing reports for project stakeholders, writing the conference publication, preparing the conference presentation and presenting.
-
Pfister, Joachim and Schwabe, Gerhard (2013): „The Landscape of Electronic Data Safes and Their Adoption in E-Government and E-Business“. In: Proceedings of the 46th Hawaii International Conference on System Sciences (HICSS). January 7 – January 10 2013. Wailea, Maui, Hawaii., United States. 1963–1972, DOI: 10.1109/HICSS.2013.532. (PDF online @ institutional repository of University of Zurich)
Abstract of: The Landscape of Electronic Data Safes and Their Adoption in E-Government and E-Business
This article reports on the concept of electronic data safes for managing personal data and describes the landscape of existing services. Using an exploratory research approach, a model of hierarchical service layers is developed. It serves as a structure for orientation in this emerging field of tools and services. Furthermore, we identify factors and areas of interest that are relevant for the adoption of electronic data safes in e-government and e-business using the Unified Theory of Acceptance and Use of Technology as a theoretical lens. We conclude that clearly perceivable benefits are key facilitators for the adoption of electronic data safes by end-users.
-
An extended analysis of the business models for electronic data safes can be found in chapter 2.4 of my thesis.
Pfister, Joachim (2017): Electronic Data Safes – Personal Information Management at the Intersection of Electronic Process Support and User-Managed Access in E-Business and E-Government. PhD thesis. University of Zurich. PDF eDiss UZH.